RP
Size: a a a
2020 June 30
на фортике инпут с микрота разрешен?
Там он видит Hello от MT, он их на MT от Fortinet не видит
B
Там он видит Hello от MT, он их на MT от Fortinet не видит
Значит фаерволл, 100%.
Была у меня тоже такая штука.
Была у меня тоже такая штука.
СК
Вы порядок правил привели к виду, как у меня в примере или оставили свой?
У вас очевидно, что на OUTPUT пакеты уходят, а на INPUT до OSPF процесса они уже не добираются, значит их блокирует фаервол
У вас очевидно, что на OUTPUT пакеты уходят, а на INPUT до OSPF процесса они уже не добираются, значит их блокирует фаервол
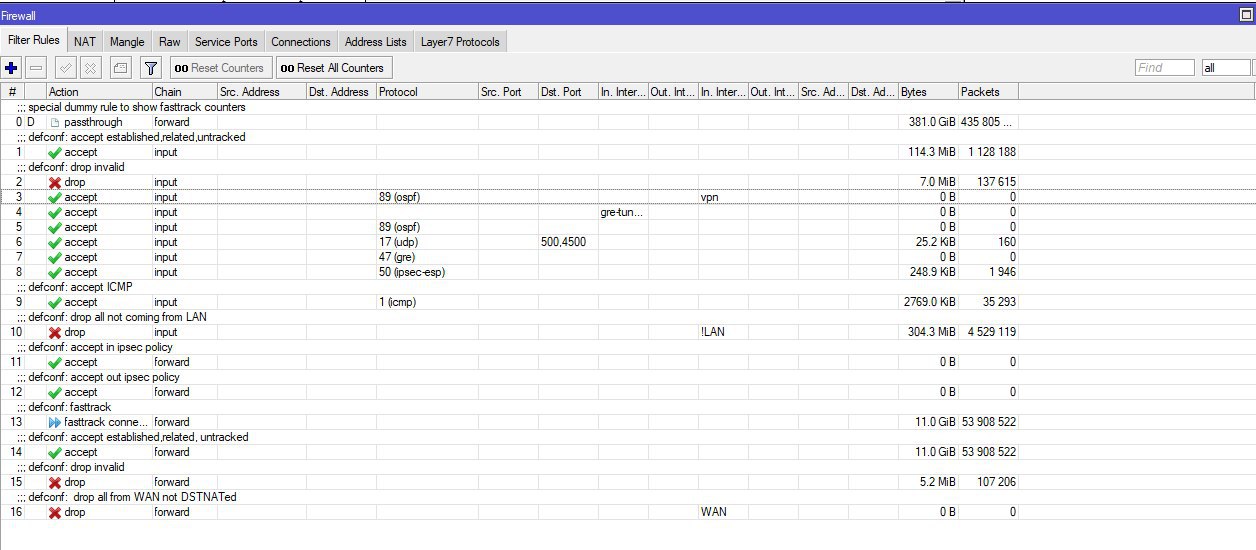
меня еще смущает, что счётчик gre по 0
СК
В RAW никаких правил нет?
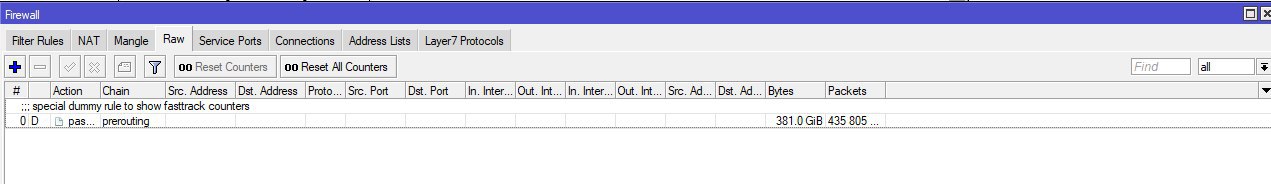
RP
Значит фаерволл, 100%.
Была у меня тоже такая штука.
Была у меня тоже такая штука.
Она у всех была наверное, хоть раз в жизни 👍 сам так же на одном из spoke забыв добавить правило в фаервол, смотря на ассиметричные hello пакеты и долго думал 😃
СК
на фортике инпут с микрота разрешен?
да, там у меня туннель закинут в зону SDWAN к другим туннелям, и для зоны есть правила, разрешающие любой трафик как между участниками зоны, так и в LAN-зону.
это пока тестовая инсталляция, поэтому файрвол открыт по-максимуму
это пока тестовая инсталляция, поэтому файрвол открыт по-максимуму
RP
Сергей Краснов

меня еще смущает, что счётчик gre по 0
Это нормально, поскольку маршрутизатор устанавливает соединение самостоятельно, на OUTPUT то создаёт в connection tracking запись и данное правило уже не затрагивается для пакета.
DS
Сергей Краснов

меня еще смущает, что счётчик gre по 0
ну gre же явно выше invalid должно быть, сколько можно-то :)
СК
ну gre же явно выше invalid должно быть, сколько можно-то :)
так и было, это я сейчас перетасовал правила для проверки. сейчас верну обратно
RP
ну gre же явно выше invalid должно быть, сколько можно-то :)
У него OSPF направляя Hello трегирит GRE и тот создаёт в connection tracking запись, поэтому GRE не будет попадать в invalid.
RP
Сергей Краснов
так и было, это я сейчас перетасовал правила для проверки. сейчас верну обратно
Я вам с работающей сети привёл пример, только там одни MT.
[polukhinri@ccr1016-grt01-sib] > routing ospf neighbor print
0 instance=default router-id=172.16.0.131 address=172.16.0.10 interface=gre-tunnel3 priority=1 dr-address=0.0.0.0 backup-dr-address=0.0.0.0 state="Full" state-changes=5 ls-retransmits=0 ls-requests=0 db-summaries=0 adjacency=6d17h22m13s
[polukhinri@ccr1016-grt01-sib] > routing ospf neighbor print
0 instance=default router-id=172.16.0.131 address=172.16.0.10 interface=gre-tunnel3 priority=1 dr-address=0.0.0.0 backup-dr-address=0.0.0.0 state="Full" state-changes=5 ls-retransmits=0 ls-requests=0 db-summaries=0 adjacency=6d17h22m13s
СК
создал правило input без дополнительных условий, выше всех прочих - всё равно не помогает
DS
Сергей Краснов
создал правило input без дополнительных условий, выше всех прочих - всё равно не помогает
/interface gre export
RP
Сергей Краснов
создал правило input без дополнительных условий, выше всех прочих - всё равно не помогает
Я вижу вы используете ESP в tunnel mode, почему не transport?
СК
/interface gre export
DS
СК
Я вижу вы используете ESP в tunnel mode, почему не transport?
по другому не заработало, не могу сказать, почему. для меня ipsec пока не полностью понятен, особенно в MT
МФ
Может. Зависит от размера оплаты и точности постановки задачи.
Больше зависит от скила...
СК
/ip ipsec export verbose
здесь 1.1.1.1 - Фортик, 2,2,2,2 - Микротик
/ip ipsec export verbose
# jun/30/2020 16:07:42 by RouterOS 6.46.4
# software id = Q9RL-ZLT3
#
# model = RB952Ui-5ac2nD
# serial number = 71AF0A2FCF47
/ip ipsec mode-config
set [ find default=yes ] name=request-only responder=no
/ip ipsec policy group
set [ find default=yes ] name=default
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024 dpd-interval=2m \
dpd-maximum-failures=5 enc-algorithm=aes-128,3des hash-algorithm=sha1 \
lifetime=1d name=default nat-traversal=yes proposal-check=obey
add dh-group=modp2048,modp1536,modp1024 dpd-interval=2m dpd-maximum-failures=5 \
enc-algorithm=aes-128,3des hash-algorithm=sha256 lifetime=1d name=ipsec-ph1 \
nat-traversal=yes proposal-check=obey
/ip ipsec peer
add address=1.1.1.1/32 disabled=no exchange-mode=ike2 local-address=\
2.2.2.2 name=ipsec-peer1 passive=yes profile=ipsec-ph1 \
send-initial-contact=yes
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha1 disabled=no enc-algorithms=\
aes-256-cbc,aes-192-cbc,aes-128-cbc lifetime=12h name=default pfs-group=\
modp1536
add auth-algorithms=sha256,sha1 disabled=no enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add auth-method=pre-shared-key disabled=no generate-policy=port-override peer=\
ipsec-peer1 secret=123456Qq
/ip ipsec policy
set 0 disabled=no dst-address=::/0 group=default proposal=default protocol=all \
src-address=::/0 template=yes
add action=encrypt disabled=no dst-address=0.0.0.0/0 dst-port=any \
ipsec-protocols=esp level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
protocol=all sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 \
src-address=10.255.10.2/32 src-port=any tunnel=yes
/ip ipsec settings
set accounting=yes interim-update=0s xauth-use-radius=no
/ip ipsec export verbose
# jun/30/2020 16:07:42 by RouterOS 6.46.4
# software id = Q9RL-ZLT3
#
# model = RB952Ui-5ac2nD
# serial number = 71AF0A2FCF47
/ip ipsec mode-config
set [ find default=yes ] name=request-only responder=no
/ip ipsec policy group
set [ find default=yes ] name=default
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024 dpd-interval=2m \
dpd-maximum-failures=5 enc-algorithm=aes-128,3des hash-algorithm=sha1 \
lifetime=1d name=default nat-traversal=yes proposal-check=obey
add dh-group=modp2048,modp1536,modp1024 dpd-interval=2m dpd-maximum-failures=5 \
enc-algorithm=aes-128,3des hash-algorithm=sha256 lifetime=1d name=ipsec-ph1 \
nat-traversal=yes proposal-check=obey
/ip ipsec peer
add address=1.1.1.1/32 disabled=no exchange-mode=ike2 local-address=\
2.2.2.2 name=ipsec-peer1 passive=yes profile=ipsec-ph1 \
send-initial-contact=yes
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha1 disabled=no enc-algorithms=\
aes-256-cbc,aes-192-cbc,aes-128-cbc lifetime=12h name=default pfs-group=\
modp1536
add auth-algorithms=sha256,sha1 disabled=no enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add auth-method=pre-shared-key disabled=no generate-policy=port-override peer=\
ipsec-peer1 secret=123456Qq
/ip ipsec policy
set 0 disabled=no dst-address=::/0 group=default proposal=default protocol=all \
src-address=::/0 template=yes
add action=encrypt disabled=no dst-address=0.0.0.0/0 dst-port=any \
ipsec-protocols=esp level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
protocol=all sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 \
src-address=10.255.10.2/32 src-port=any tunnel=yes
/ip ipsec settings
set accounting=yes interim-update=0s xauth-use-radius=no
DS
Сергей Краснов
здесь 1.1.1.1 - Фортик, 2,2,2,2 - Микротик
/ip ipsec export verbose
# jun/30/2020 16:07:42 by RouterOS 6.46.4
# software id = Q9RL-ZLT3
#
# model = RB952Ui-5ac2nD
# serial number = 71AF0A2FCF47
/ip ipsec mode-config
set [ find default=yes ] name=request-only responder=no
/ip ipsec policy group
set [ find default=yes ] name=default
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024 dpd-interval=2m \
dpd-maximum-failures=5 enc-algorithm=aes-128,3des hash-algorithm=sha1 \
lifetime=1d name=default nat-traversal=yes proposal-check=obey
add dh-group=modp2048,modp1536,modp1024 dpd-interval=2m dpd-maximum-failures=5 \
enc-algorithm=aes-128,3des hash-algorithm=sha256 lifetime=1d name=ipsec-ph1 \
nat-traversal=yes proposal-check=obey
/ip ipsec peer
add address=1.1.1.1/32 disabled=no exchange-mode=ike2 local-address=\
2.2.2.2 name=ipsec-peer1 passive=yes profile=ipsec-ph1 \
send-initial-contact=yes
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha1 disabled=no enc-algorithms=\
aes-256-cbc,aes-192-cbc,aes-128-cbc lifetime=12h name=default pfs-group=\
modp1536
add auth-algorithms=sha256,sha1 disabled=no enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add auth-method=pre-shared-key disabled=no generate-policy=port-override peer=\
ipsec-peer1 secret=123456Qq
/ip ipsec policy
set 0 disabled=no dst-address=::/0 group=default proposal=default protocol=all \
src-address=::/0 template=yes
add action=encrypt disabled=no dst-address=0.0.0.0/0 dst-port=any \
ipsec-protocols=esp level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
protocol=all sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 \
src-address=10.255.10.2/32 src-port=any tunnel=yes
/ip ipsec settings
set accounting=yes interim-update=0s xauth-use-radius=no
/ip ipsec export verbose
# jun/30/2020 16:07:42 by RouterOS 6.46.4
# software id = Q9RL-ZLT3
#
# model = RB952Ui-5ac2nD
# serial number = 71AF0A2FCF47
/ip ipsec mode-config
set [ find default=yes ] name=request-only responder=no
/ip ipsec policy group
set [ find default=yes ] name=default
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024 dpd-interval=2m \
dpd-maximum-failures=5 enc-algorithm=aes-128,3des hash-algorithm=sha1 \
lifetime=1d name=default nat-traversal=yes proposal-check=obey
add dh-group=modp2048,modp1536,modp1024 dpd-interval=2m dpd-maximum-failures=5 \
enc-algorithm=aes-128,3des hash-algorithm=sha256 lifetime=1d name=ipsec-ph1 \
nat-traversal=yes proposal-check=obey
/ip ipsec peer
add address=1.1.1.1/32 disabled=no exchange-mode=ike2 local-address=\
2.2.2.2 name=ipsec-peer1 passive=yes profile=ipsec-ph1 \
send-initial-contact=yes
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha1 disabled=no enc-algorithms=\
aes-256-cbc,aes-192-cbc,aes-128-cbc lifetime=12h name=default pfs-group=\
modp1536
add auth-algorithms=sha256,sha1 disabled=no enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add auth-method=pre-shared-key disabled=no generate-policy=port-override peer=\
ipsec-peer1 secret=123456Qq
/ip ipsec policy
set 0 disabled=no dst-address=::/0 group=default proposal=default protocol=all \
src-address=::/0 template=yes
add action=encrypt disabled=no dst-address=0.0.0.0/0 dst-port=any \
ipsec-protocols=esp level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
protocol=all sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 \
src-address=10.255.10.2/32 src-port=any tunnel=yes
/ip ipsec settings
set accounting=yes interim-update=0s xauth-use-radius=no
с другой стороны policy - фаза два симметрична ?



