RP
Size: a a a
2020 June 30
Добрый день всем! Подскажите какой режим агрегации на микротике соответствует LACP ? Есть коммутатор HP5500, есть микротик CCR1036, необходимо между ними сделать агрегацию. С HP вроде разобрался, создал интерфейс BridgeAggregation и включил в него нужные порты, а на CCR не пойму какой bonding mode выбрать. Задача сделать линк пропускной способностью больше 1гб
802.3ad, согласно версии стандарта описывающего данный протокол
AS
Да атака на днс уже в прошлом)
провайдеры могут начать банить все неугодные днс сервера) и все и заставить работать только через свой
АД
Сергей Краснов
конфига:
/interface gre
add allow-fast-path=no !keepalive local-address=2.2.2.2 name=\
gre-tunnel1 remote-address=1.1.1.1
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024
add dh-group=modp2048,modp1536,modp1024 hash-algorithm=sha256 name=ipsec-ph1
/ip ipsec peer
add address=1.1.1.1/32 exchange-mode=ike2 local-address=2.2.2.2 \
name=ipsec-peer1 passive=yes profile=ipsec-ph1
/ip ipsec proposal
set [ find default=yes ] lifetime=12h pfs-group=modp1536
add auth-algorithms=sha256,sha1 enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add generate-policy=port-strict peer=ipsec-peer1 secret=1234567890
/ip ipsec policy
add dst-address=0.0.0.0/0 level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 src-address=\
10.255.10.2/32 tunnel=yes
/routing ospf area
add area-id=0.0.0.88 name=area1
/routing ospf instance
set [ find default=yes ] router-id=192.168.88.1
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
add address=10.255.10.2/30 interface=gre-tunnel1 network=10.255.10.0
/routing ospf network
add area=backbone network=10.255.0.0/16
add area=area1 network=192.168.88.0/24
/ip firewall filter
add action=accept chain=input dst-port=500,4500 protocol=udp
add action=accept chain=input protocol=gre
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat out-interface=gre-tunnel1
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
/interface gre
add allow-fast-path=no !keepalive local-address=2.2.2.2 name=\
gre-tunnel1 remote-address=1.1.1.1
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024
add dh-group=modp2048,modp1536,modp1024 hash-algorithm=sha256 name=ipsec-ph1
/ip ipsec peer
add address=1.1.1.1/32 exchange-mode=ike2 local-address=2.2.2.2 \
name=ipsec-peer1 passive=yes profile=ipsec-ph1
/ip ipsec proposal
set [ find default=yes ] lifetime=12h pfs-group=modp1536
add auth-algorithms=sha256,sha1 enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add generate-policy=port-strict peer=ipsec-peer1 secret=1234567890
/ip ipsec policy
add dst-address=0.0.0.0/0 level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 src-address=\
10.255.10.2/32 tunnel=yes
/routing ospf area
add area-id=0.0.0.88 name=area1
/routing ospf instance
set [ find default=yes ] router-id=192.168.88.1
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
add address=10.255.10.2/30 interface=gre-tunnel1 network=10.255.10.0
/routing ospf network
add area=backbone network=10.255.0.0/16
add area=area1 network=192.168.88.0/24
/ip firewall filter
add action=accept chain=input dst-port=500,4500 protocol=udp
add action=accept chain=input protocol=gre
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat out-interface=gre-tunnel1
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
fw input ospf?
DS
Сергей Краснов
конфига:
/interface gre
add allow-fast-path=no !keepalive local-address=2.2.2.2 name=\
gre-tunnel1 remote-address=1.1.1.1
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024
add dh-group=modp2048,modp1536,modp1024 hash-algorithm=sha256 name=ipsec-ph1
/ip ipsec peer
add address=1.1.1.1/32 exchange-mode=ike2 local-address=2.2.2.2 \
name=ipsec-peer1 passive=yes profile=ipsec-ph1
/ip ipsec proposal
set [ find default=yes ] lifetime=12h pfs-group=modp1536
add auth-algorithms=sha256,sha1 enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add generate-policy=port-strict peer=ipsec-peer1 secret=1234567890
/ip ipsec policy
add dst-address=0.0.0.0/0 level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 src-address=\
10.255.10.2/32 tunnel=yes
/routing ospf area
add area-id=0.0.0.88 name=area1
/routing ospf instance
set [ find default=yes ] router-id=192.168.88.1
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
add address=10.255.10.2/30 interface=gre-tunnel1 network=10.255.10.0
/routing ospf network
add area=backbone network=10.255.0.0/16
add area=area1 network=192.168.88.0/24
/ip firewall filter
add action=accept chain=input dst-port=500,4500 protocol=udp
add action=accept chain=input protocol=gre
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat out-interface=gre-tunnel1
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
/interface gre
add allow-fast-path=no !keepalive local-address=2.2.2.2 name=\
gre-tunnel1 remote-address=1.1.1.1
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024
add dh-group=modp2048,modp1536,modp1024 hash-algorithm=sha256 name=ipsec-ph1
/ip ipsec peer
add address=1.1.1.1/32 exchange-mode=ike2 local-address=2.2.2.2 \
name=ipsec-peer1 passive=yes profile=ipsec-ph1
/ip ipsec proposal
set [ find default=yes ] lifetime=12h pfs-group=modp1536
add auth-algorithms=sha256,sha1 enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add generate-policy=port-strict peer=ipsec-peer1 secret=1234567890
/ip ipsec policy
add dst-address=0.0.0.0/0 level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 src-address=\
10.255.10.2/32 tunnel=yes
/routing ospf area
add area-id=0.0.0.88 name=area1
/routing ospf instance
set [ find default=yes ] router-id=192.168.88.1
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
add address=10.255.10.2/30 interface=gre-tunnel1 network=10.255.10.0
/routing ospf network
add area=backbone network=10.255.0.0/16
add area=area1 network=192.168.88.0/24
/ip firewall filter
add action=accept chain=input dst-port=500,4500 protocol=udp
add action=accept chain=input protocol=gre
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat out-interface=gre-tunnel1
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
зачем натить с out-interface = gre?
gre в лист LAN
gre в лист LAN
B
Сергей Краснов
Всем привет, подскажите, пожалуйста, в чем может быть проблема в такой ситуации:
Пытаюсь заставить работать схему с IPSEC-GRE туннелем между Mikrotik и Fortigate, с OSPF-маршрутизацией поверх.
На данный момент Ph1 и Ph2 поднимаются, пинги ходят в обе стороны, Fortigate OSPF получает hello от Микротика, а вот Микротик hello-пакеты, видимо, не получает. Со стороны Фортика делаю захват трафика на туннельном интерфейсе и вижу, как Hello идут в обе стороны, со стороны Микротика как захватить пакеты - не понимаю, ни packet sniffer, ни torch на gre-интерфейсе ничего не показывают.
Пытаюсь заставить работать схему с IPSEC-GRE туннелем между Mikrotik и Fortigate, с OSPF-маршрутизацией поверх.
На данный момент Ph1 и Ph2 поднимаются, пинги ходят в обе стороны, Fortigate OSPF получает hello от Микротика, а вот Микротик hello-пакеты, видимо, не получает. Со стороны Фортика делаю захват трафика на туннельном интерфейсе и вижу, как Hello идут в обе стороны, со стороны Микротика как захватить пакеты - не понимаю, ни packet sniffer, ни torch на gre-интерфейсе ничего не показывают.
если дефалтовый фаер на микроте, то разрешить входящий трафик с адреса туннельного интерфейса на микроте
B
зачем натить с out-interface = gre?
gre в лист LAN
gre в лист LAN
как вариант
СК
зачем натить с out-interface = gre?
gre в лист LAN
gre в лист LAN
прочитал в одной из статей по ipsec в mikrotik, что ipsec применяется уже после src-nat, и что, если настроено общее правило src-nat для всего трафика в интернет, то ipsec, мол, не применится, поэтому нужно создавать правило с действием accept для всего трафика, который может идти через туннель.
или я неправильно понял что-то?
или я неправильно понял что-то?
СК
fw input ospf?
не помогло : (
DS
Сергей Краснов
прочитал в одной из статей по ipsec в mikrotik, что ipsec применяется уже после src-nat, и что, если настроено общее правило src-nat для всего трафика в интернет, то ipsec, мол, не применится, поэтому нужно создавать правило с действием accept для всего трафика, который может идти через туннель.
или я неправильно понял что-то?
или я неправильно понял что-то?
а да, я не внимательно прочитал
DS
Сергей Краснов
не помогло : (
gre в лист LAN
СК
gre в лист LAN
если не сложно, расскажите подробнее - я не понял, где это и что
СК
если дефалтовый фаер на микроте, то разрешить входящий трафик с адреса туннельного интерфейса на микроте
не помогло тоже : (
B
Сергей Краснов
если не сложно, расскажите подробнее - я не понял, где это и что
B
Сергей Краснов
не помогло тоже : (
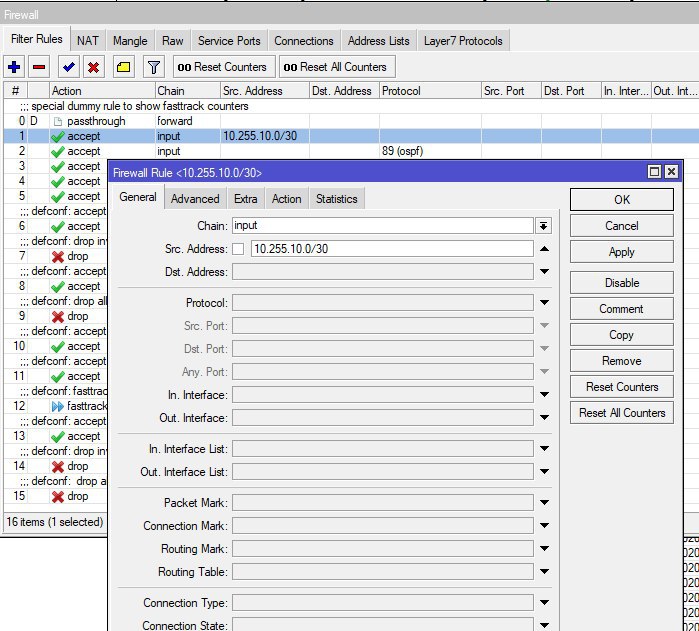
правило покажите
RP
Сергей Краснов
конфига:
/interface gre
add allow-fast-path=no !keepalive local-address=2.2.2.2 name=\
gre-tunnel1 remote-address=1.1.1.1
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024
add dh-group=modp2048,modp1536,modp1024 hash-algorithm=sha256 name=ipsec-ph1
/ip ipsec peer
add address=1.1.1.1/32 exchange-mode=ike2 local-address=2.2.2.2 \
name=ipsec-peer1 passive=yes profile=ipsec-ph1
/ip ipsec proposal
set [ find default=yes ] lifetime=12h pfs-group=modp1536
add auth-algorithms=sha256,sha1 enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add generate-policy=port-strict peer=ipsec-peer1 secret=1234567890
/ip ipsec policy
add dst-address=0.0.0.0/0 level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 src-address=\
10.255.10.2/32 tunnel=yes
/routing ospf area
add area-id=0.0.0.88 name=area1
/routing ospf instance
set [ find default=yes ] router-id=192.168.88.1
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
add address=10.255.10.2/30 interface=gre-tunnel1 network=10.255.10.0
/routing ospf network
add area=backbone network=10.255.0.0/16
add area=area1 network=192.168.88.0/24
/ip firewall filter
add action=accept chain=input dst-port=500,4500 protocol=udp
add action=accept chain=input protocol=gre
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat out-interface=gre-tunnel1
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
/interface gre
add allow-fast-path=no !keepalive local-address=2.2.2.2 name=\
gre-tunnel1 remote-address=1.1.1.1
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536,modp1024
add dh-group=modp2048,modp1536,modp1024 hash-algorithm=sha256 name=ipsec-ph1
/ip ipsec peer
add address=1.1.1.1/32 exchange-mode=ike2 local-address=2.2.2.2 \
name=ipsec-peer1 passive=yes profile=ipsec-ph1
/ip ipsec proposal
set [ find default=yes ] lifetime=12h pfs-group=modp1536
add auth-algorithms=sha256,sha1 enc-algorithms=\
aes-128-cbc,aes-128-ctr,aes-128-gcm,camellia-128 lifetime=12h name=\
ipsec-ph2 pfs-group=modp1536
/ip ipsec identity
add generate-policy=port-strict peer=ipsec-peer1 secret=1234567890
/ip ipsec policy
add dst-address=0.0.0.0/0 level=unique peer=ipsec-peer1 proposal=ipsec-ph2 \
sa-dst-address=1.1.1.1 sa-src-address=2.2.2.2 src-address=\
10.255.10.2/32 tunnel=yes
/routing ospf area
add area-id=0.0.0.88 name=area1
/routing ospf instance
set [ find default=yes ] router-id=192.168.88.1
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
add address=10.255.10.2/30 interface=gre-tunnel1 network=10.255.10.0
/routing ospf network
add area=backbone network=10.255.0.0/16
add area=area1 network=192.168.88.0/24
/ip firewall filter
add action=accept chain=input dst-port=500,4500 protocol=udp
add action=accept chain=input protocol=gre
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat out-interface=gre-tunnel1
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
Лишнее убрал
[polukhinri@ccr1016-grt01-sib] /ip firewall filter> print
Flags: X - disabled, I - invalid, D - dynamic
0 D ;;; special dummy rule to show fasttrack counters
chain=forward action=passthrough
1 ;;; accept established, related, untracked
chain=input action=accept connection-state=established,related,untracked log=no log-prefix=""
2 ;;; drop invalid
chain=input action=drop connection-state=invalid log=no log-prefix=""
3 ;;; accept OSPF
chain=input action=accept protocol=ospf in-interface-list=VPN log=no log-prefix=""
5 ;;; accept IKE, IPsec ESP over UDP
chain=input action=accept protocol=udp in-interface-list=WAN dst-port=500,4500 log=no log-prefix=""
6 ;;; accept IPsec ESP
chain=input action=accept protocol=ipsec-esp in-interface-list=WAN log=no log-prefix=""
7 ;;; accept GRE
chain=input action=accept protocol=gre in-interface-list=WAN log=no log-prefix="" ipsec-policy=in,ipsec
15 ;;; drop all not coming from LAN
chain=input action=drop in-interface-list=!LAN log=no log-prefix=""
[polukhinri@ccr1016-grt01-sib] /ip firewall nat> print
Flags: X - disabled, I - invalid, D - dynamic
0 ;;; src-nat from LAN to WAN
chain=srcnat action=src-nat to-addresses=X.X.X.X out-interface-list=WAN log=no log-prefix=""
[polukhinri@ccr1016-grt01-sib] /interface list member> print
Flags: X - disabled, D - dynamic
# LIST INTERFACE
3 VPN gre-tunnel1
4 VPN gre-tunnel2
5 VPN gre-tunnel3
[polukhinri@ccr1016-grt01-sib] /ip firewall filter> print
Flags: X - disabled, I - invalid, D - dynamic
0 D ;;; special dummy rule to show fasttrack counters
chain=forward action=passthrough
1 ;;; accept established, related, untracked
chain=input action=accept connection-state=established,related,untracked log=no log-prefix=""
2 ;;; drop invalid
chain=input action=drop connection-state=invalid log=no log-prefix=""
3 ;;; accept OSPF
chain=input action=accept protocol=ospf in-interface-list=VPN log=no log-prefix=""
5 ;;; accept IKE, IPsec ESP over UDP
chain=input action=accept protocol=udp in-interface-list=WAN dst-port=500,4500 log=no log-prefix=""
6 ;;; accept IPsec ESP
chain=input action=accept protocol=ipsec-esp in-interface-list=WAN log=no log-prefix=""
7 ;;; accept GRE
chain=input action=accept protocol=gre in-interface-list=WAN log=no log-prefix="" ipsec-policy=in,ipsec
15 ;;; drop all not coming from LAN
chain=input action=drop in-interface-list=!LAN log=no log-prefix=""
[polukhinri@ccr1016-grt01-sib] /ip firewall nat> print
Flags: X - disabled, I - invalid, D - dynamic
0 ;;; src-nat from LAN to WAN
chain=srcnat action=src-nat to-addresses=X.X.X.X out-interface-list=WAN log=no log-prefix=""
[polukhinri@ccr1016-grt01-sib] /interface list member> print
Flags: X - disabled, D - dynamic
# LIST INTERFACE
3 VPN gre-tunnel1
4 VPN gre-tunnel2
5 VPN gre-tunnel3
СК
B
а зачем всю подсеть то, разрешите только адрес с фортигейт
DS
Сергей Краснов
если не сложно, расскажите подробнее - я не понял, где это и что
/interface list member add interface=gre-tunnel1 list=LAN
СК
а зачем всю подсеть то, разрешите только адрес с фортигейт
так тоже не сработало
СК
/interface list member add interface=gre-tunnel1 list=LAN
не помогло : (