SI
Size: a a a
2019 July 06
Лучше самому решить)
Верно!
DM
Там таск лёгенький по вебу чтобы кто попало не заходил, я скрипт на питоне навоял чтобы не парится https://securixy.kz/hack-faq/ctf/hackthebox-kak-poluchit-invite-kod.html/
легкий для вебера, трудный для бинарщика))))
T
Кто по реверсу силён, помогите понять таск на ХТБ https://www.hackthebox.eu/home/challenges/Reversing
Debugme
Debugme
ТАм используются anti-debugging техники
DM
но спасибо за блог, позже почитаю
T
Кто по реверсу силён, помогите понять таск на ХТБ https://www.hackthebox.eu/home/challenges/Reversing
Debugme
Debugme
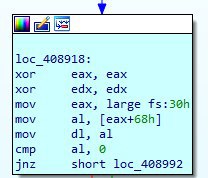
В самом начале, берется адрес блока PEB, и добавляется 2. Таким образом берется значение поля BeingDebugged
T
typedef struct _PEB {
BYTE Reserved1[2];
BYTE BeingDebugged;Вот тут видишь, он вторым полем идет. Если программа запущена под дебагером, то там стоит флаг, что присутствует дебагер.
T
Просто запачь этот кусок и всё
T
Я помню в IDA, писал такой мини скрипт
#Стартует приложение!
RunTo(BeginEA());
GetDebuggerEvent(WFNE_SUSP, -1);
# На старте, EBX содержит адрес структуры PEB.
ebx_addr = idc.GetRegValue('EBX')
PatchByte(ebx_addr + 2, 0);
print "BeingDebugged field in PEB patched!"
T
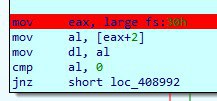
Я про это место
T
Далее идет другая антидебаг техника
PEB!NtGlobalFlags
When a process is created, the system sets some flags that will define how various APIs will behave for this program. Those flags can be read in the PEB, in the DWORD located at offset 0x68 (see the reference).
By default, different flags are set depending if the process is created under a debugger or not. If the process is debugged, some flags controlling the heap manipulation routines in ntdll will be set: FLG_HEAP_ENABLE_TAIL_CHECK, FLG_HEAP_ENABLE_FREE_CHECK and FLG_HEAP_VALIDATE_PARAMETERS.
This anti-debug can be bypassed by resetting the NtGlobalFlags field.
T
+0x68
T
Тоже можно запатчить
T
Дальше не смотрел, пока времени нет*(
T
Ну и судя по тексту к заданию, можно понять, что антидебаг какой-то есть
T
Я писал такой код на питоне для IDA, чтобы автоматически обходить такое
https://pastebin.com/W3UbPxEQ
Да, коряво возможно и топорно, но работало)
https://pastebin.com/W3UbPxEQ
Да, коряво возможно и топорно, но работало)
T
Добро пожаловать)
Z
Добро пожаловать)
Привет всем
R
Приветствую 🖖🏻