SG
Size: a a a
2020 March 17
А. понял
k
Проще всего посмотреть пользователя, от кого созданы и отдаются Файлы приложения через ls -lah
Покажет владельца
Покажет владельца
k
Теперь, зная пользователя, в каталоге с nc выполняй
sudo -u www-data (или от какого юзера запускается nc, которого в выводе ls -lah видел) php occ maintenance:false
sudo -u www-data (или от какого юзера запускается nc, которого в выводе ls -lah видел) php occ maintenance:false
k
Команду разобрать, что она выполняет?
ББ
k
Изи. Скажи свой email, на который деньги переводить 😂
ББ
🥓Э
Изи. Скажи свой email, на который деньги переводить 😂
Самое забавное, что когда родилась эта фраза такое не было реализовано)
🥓Э
Из Хоттабыча что-ли?
k
Самое забавное, что когда родилась эта фраза такое не было реализовано)
Это из фильма Хоттабыч же)
SG
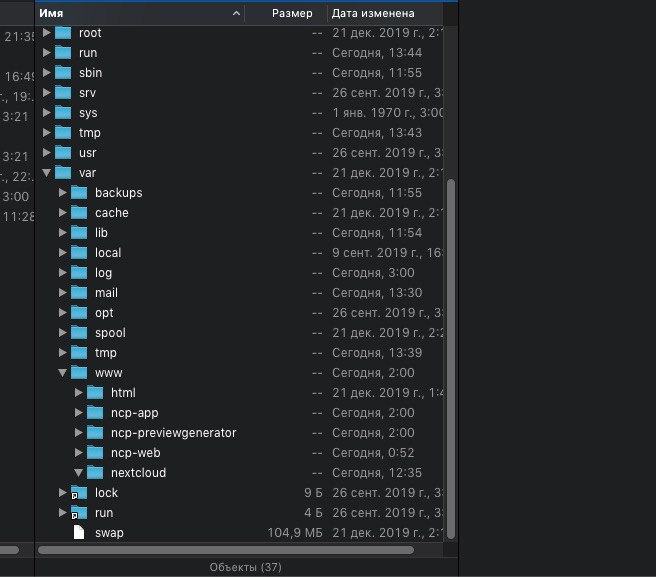
нифига не разберусь
нет каталга nc
lock и run
нет каталга nc
lock и run
SG
конфига нигде нет
ББ
У него ncp если што
SG
S
Dear Customers,
In the last 24 hours, a new security risk was reported that affects remote wipe in Nextcloud 17 and 18. This vulnerability allows an attacker to execute remote wipe on devices from other users. No data is deleted or leaked. This does not affect Nextcloud releases before 17 which do not contain the Remote Wipe feature.
We provide 2 patches that fix this issue. Minor releases will be made available early next week as well. Read on for details to help you decide if patching or an unscheduled update is needed.
Details
To exploit the vulnerability, a malicious user needs to have an account on your Nextcloud server. This can be a guest account (but not a user with just a public link).
The malicious user can then craft a special request which remote-wipes the devices of all users on the server by iterating over them. This is user id independent, that is, the malicious user can not target any specific user but merely wipe randomly or all devices from all users on the server one by one.
Note: no data is lost or leaked, users will only have to re-create their user account and re-download all their data. As this can cause lost time and effort as well as heavy server load, this is essentially a service-degrading attack.
On larger instances, monitoring would show a malicious user who would be doing this, because they would need to send a large number of requests to the server which results in a lot of 404 and 400 responses. We would recommend temporarily disabling an accounts showing such activity.
Download the patches here.
Early next week (currently scheduled for Monday) a security update for Nextcloud 17 and 18 will be made available. Depending on your risk assessment or if patching is not feasible, you can plan maintenance to install these updates when they become available.
If you need any help, please reach out to our support team! You can use our portal or just reply to this email.
Thanks for your attention,
Your Nextcloud Security team
In the last 24 hours, a new security risk was reported that affects remote wipe in Nextcloud 17 and 18. This vulnerability allows an attacker to execute remote wipe on devices from other users. No data is deleted or leaked. This does not affect Nextcloud releases before 17 which do not contain the Remote Wipe feature.
We provide 2 patches that fix this issue. Minor releases will be made available early next week as well. Read on for details to help you decide if patching or an unscheduled update is needed.
Details
To exploit the vulnerability, a malicious user needs to have an account on your Nextcloud server. This can be a guest account (but not a user with just a public link).
The malicious user can then craft a special request which remote-wipes the devices of all users on the server by iterating over them. This is user id independent, that is, the malicious user can not target any specific user but merely wipe randomly or all devices from all users on the server one by one.
Note: no data is lost or leaked, users will only have to re-create their user account and re-download all their data. As this can cause lost time and effort as well as heavy server load, this is essentially a service-degrading attack.
On larger instances, monitoring would show a malicious user who would be doing this, because they would need to send a large number of requests to the server which results in a lot of 404 and 400 responses. We would recommend temporarily disabling an accounts showing such activity.
Download the patches here.
Early next week (currently scheduled for Monday) a security update for Nextcloud 17 and 18 will be made available. Depending on your risk assessment or if patching is not feasible, you can plan maintenance to install these updates when they become available.
If you need any help, please reach out to our support team! You can use our portal or just reply to this email.
Thanks for your attention,
Your Nextcloud Security team
SG
все
SG
нашел и поправил
SG
sudo -u www-data php /var/www/nextcloud/occ maintenance:mode --off
SG
occ maintenance:false
так не работало
так не работало
SG
спасибо за помощь))