VG
Size: a a a
2020 November 23
чего не сделаешь ради трололо гошников
VG
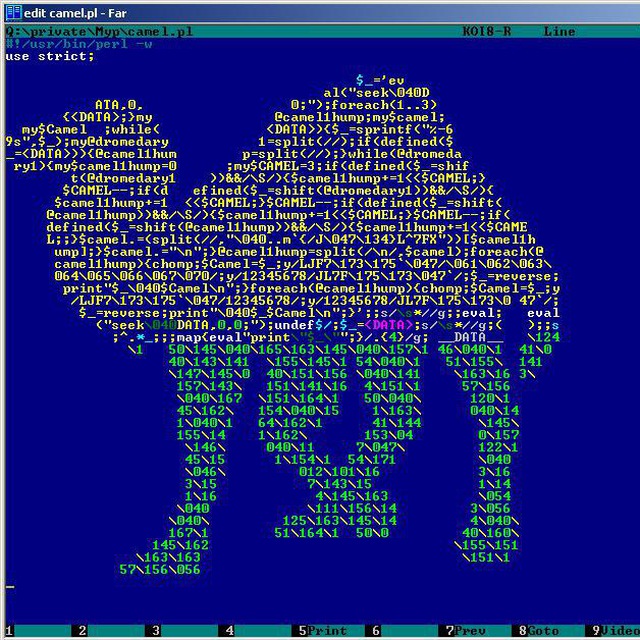
> Нет этот особый. Это зародыш SkyNet-а из фильма Терминатор.
Терминатор-сколькотам-9 ? Из будущего пачками прибывают терминаторы, которым нахрен не вcpaлась Саня Коннор, повсюду ищут и отжимают биткойн-кошелки, после чего быстро сваливают в туман, архивировать и ныкать в arctic vault под видом ценного кода с гитшлака - потому что в будущем биток стоит миллиард долларов, а новых намайнить нельзя уже всеми мощностями скайнета. Человечество будущего поробощено не оружием, а тем что скайнет просто скупил все подряд.
Главный герой - одноногая трансгендерная нигра, пытающаяся сныкать последние принадлежащие человечеству 0.00001btc.
Терминатор-сколькотам-9 ? Из будущего пачками прибывают терминаторы, которым нахрен не вcpaлась Саня Коннор, повсюду ищут и отжимают биткойн-кошелки, после чего быстро сваливают в туман, архивировать и ныкать в arctic vault под видом ценного кода с гитшлака - потому что в будущем биток стоит миллиард долларов, а новых намайнить нельзя уже всеми мощностями скайнета. Человечество будущего поробощено не оружием, а тем что скайнет просто скупил все подряд.
Главный герой - одноногая трансгендерная нигра, пытающаяся сныкать последние принадлежащие человечеству 0.00001btc.
VG
VG
сука, пора видимо озабачиваться засовыванием браузеров в jail
VG
ишь
0
One solution to the risks of X forwarding over ssh discussed in the other answers would be to use what might be called a masquerade X server, which is not really an X server but presents an pseudo X interface and a pseudo X screen to the client software on the container, while passing some X work off to the real X server behind it. The pseudo X screen is displayed as a single X window on the host actual X desktop.
Even though it wasn't intended as a security tool, Xephyr does fit that description.
For that reason I wrote a javascript program to create an lxd/lxc container from a vanilla ubuntu image, and populate it with firefox, openvpn, Xephyr, and pusleaudio.
https://github.com/craigphicks/browser-on-lxc-vpn-xephyr
https://www.npmjs.com/package/browser-on-lxc-vpn-xephyr
I wouldn't make any strong security claims about - it was a proof of concept exercise.
0
One solution to the risks of X forwarding over ssh discussed in the other answers would be to use what might be called a masquerade X server, which is not really an X server but presents an pseudo X interface and a pseudo X screen to the client software on the container, while passing some X work off to the real X server behind it. The pseudo X screen is displayed as a single X window on the host actual X desktop.
Even though it wasn't intended as a security tool, Xephyr does fit that description.
For that reason I wrote a javascript program to create an lxd/lxc container from a vanilla ubuntu image, and populate it with firefox, openvpn, Xephyr, and pusleaudio.
https://github.com/craigphicks/browser-on-lxc-vpn-xephyr
https://www.npmjs.com/package/browser-on-lxc-vpn-xephyr
I wouldn't make any strong security claims about - it was a proof of concept exercise.
YM
Орнул на работе с утра, когда коллега начал диалог с фразы: "есть два файла..."
Так должны начинаться загадки сидящих программистов.
Так должны начинаться загадки сидящих программистов.
YM
E
https://www.youtube.com/watch?v=k3qbvtRYUMY DJ Поросёнков.
MZ
Они там все ебанулись :(
MZ
✝️🏳️🌈🙈Унитарная универсалистская «христианская церковь» в Южной Каролине проводит обряд смены сексуальной идентичности детей своих последователей: маленький мальчик Феникс торжественно объявлен девочкой.
Отдельно доставляет бесполый жирный политрук-надзиратель от ЛГБТ-обкома рядом с женщиной-проповедником, а также одинокая мать Феникса, для которой смена пола её ребенка важнее всей его последующей жизни.
Шизариум.
Отдельно доставляет бесполый жирный политрук-надзиратель от ЛГБТ-обкома рядом с женщиной-проповедником, а также одинокая мать Феникса, для которой смена пола её ребенка важнее всей его последующей жизни.
Шизариум.
E
В 80-х годах гидроакустика ВМС Швеции улавливала подозрительные сигналы, которые идентифицировала как шум советских подлодок. Поисковые группы месяцами пытались найти следы вторжения, но всё безуспешно.
После развала СССР и прекращения Холодной войны, загадочные сигналы всё продолжали поступать. Поэтому шведское руководство отправило исследовательскую группу для изучения происходящего.
В 1996 году профессор Магнус Уолберг провёл исследование и выяснил, что это был звук, который издаёт селедка, когда ее плавательный пузырь сжимается и излишки газов выходят через анальный канал в виде пузырей воздуха. Такая структура уникальна, и встречается только у сельди.
15 лет военные моряки Швеции слушали как пердит селёдка.
После развала СССР и прекращения Холодной войны, загадочные сигналы всё продолжали поступать. Поэтому шведское руководство отправило исследовательскую группу для изучения происходящего.
В 1996 году профессор Магнус Уолберг провёл исследование и выяснил, что это был звук, который издаёт селедка, когда ее плавательный пузырь сжимается и излишки газов выходят через анальный канал в виде пузырей воздуха. Такая структура уникальна, и встречается только у сельди.
15 лет военные моряки Швеции слушали как пердит селёдка.
YM
YM
Всё, надо требовать переименования Python
E
E
концовочка отличная.