ID
Size: a a a
2020 June 01
клиент - микрот. микрот смотрит наружу, ip белый
EV
received proposals unacceptable понимаешь смысл?
ID
увы, но не особо.
ID
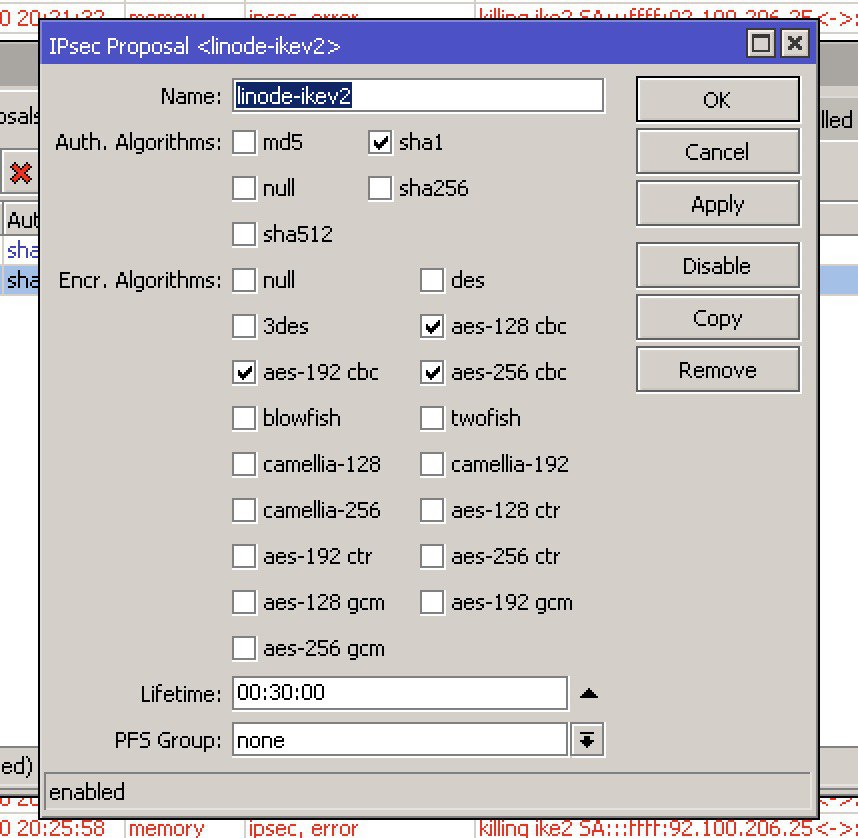
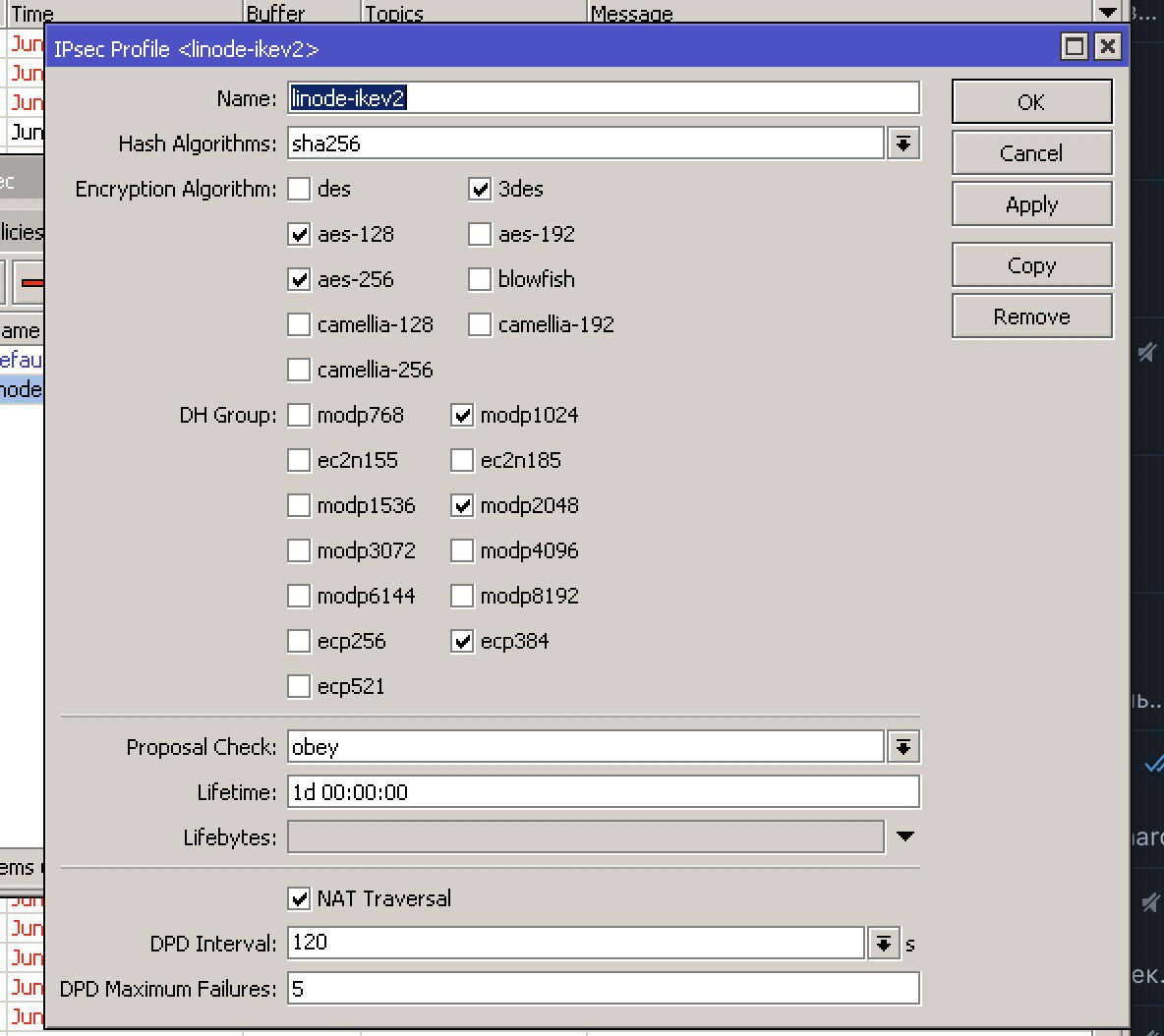
вот так у микрота сконфигурено.
EV
а на стороне сервера?
ID
ike=aes256gcm16-prfsha384-ecp384!
esp=aes256gcm16-ecp384!
ID
если я правильно смотрю
EV
вроде как правильно, только на микротике эти значения не выбраны
ID
сейчас перепроверю, спасибо
ID
выбрал в микроте aes-256 gcm
ID
в логе сервера все равно
Jun 1 17:38:48 localhost charon: 09[NET] received packet: from 92.100.206.25[4500] to 173.255.238.184[4500] (440 bytes)
Jun 1 17:38:48 localhost charon: 09[ENC] parsed IKE_SA_INIT request 0 [ N(NATD_D_IP) N(NATD_S_IP) No KE SA ]
Jun 1 17:38:48 localhost charon: 09[IKE] 92.100.206.25 is initiating an IKE_SA
Jun 1 17:38:48 localhost charon: 09[CFG] received proposals: IKE:AES_CBC_128/3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048/MODP_1024
Jun 1 17:38:48 localhost charon: 09[CFG] configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384
Jun 1 17:38:48 localhost charon: 09[IKE] faking NAT situation to enforce UDP encapsulation
Jun 1 17:38:48 localhost charon: 09[IKE] received proposals unacceptable
Jun 1 17:38:48 localhost charon: 09[ENC] generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
Jun 1 17:38:48 localhost charon: 09[NET] sending packet: from 173.255.238.184[4500] to 92.100.206.25[4500] (36 bytes)
ID
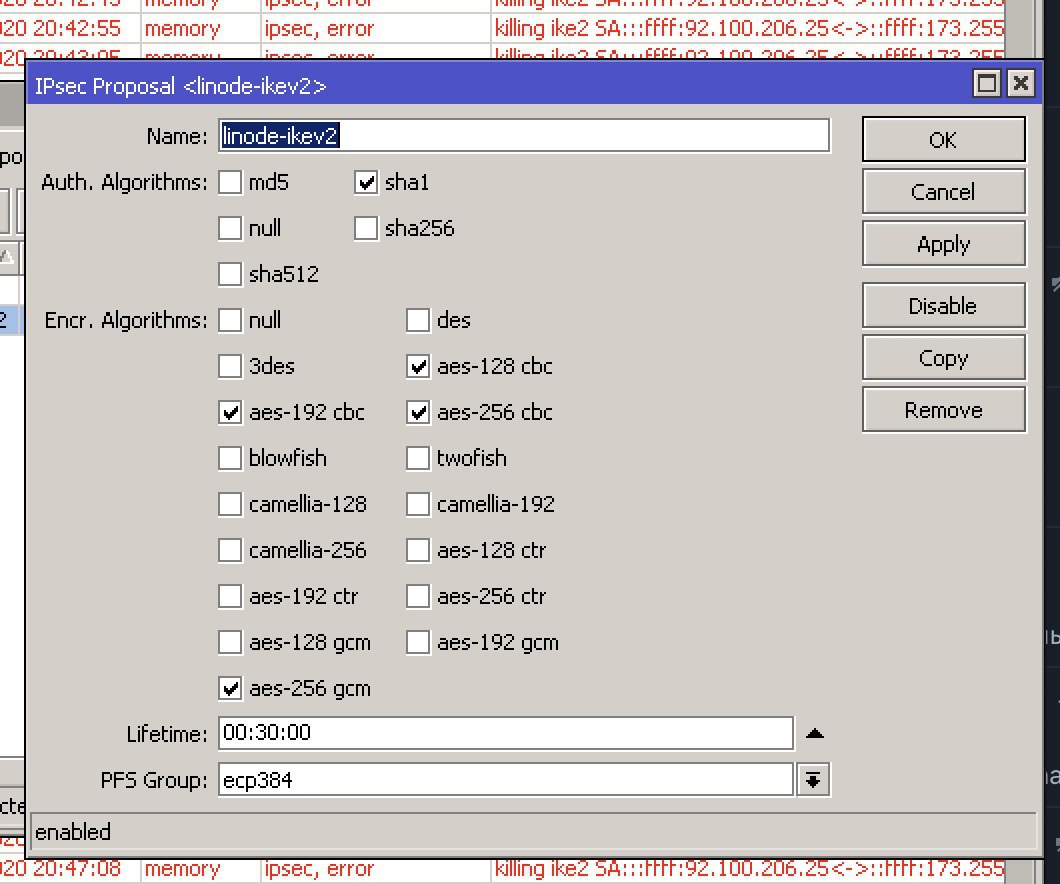
даже вот так
ID
Jun 1 17:40:21 localhost charon: 06[CFG] received proposals: IKE:AES_CBC_128/3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048/MODP_1024
Jun 1 17:40:21 localhost charon: 06[CFG] configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384
😎
у arp записей есть время жизни в таблице, так что вряд ли провайдер вам помог, скорее запись удалилась
Свою таблицу arp чистил. У провайдера могла очиститься конечно
T
А юзает кто-нибудь hEX PoE RB960PGS для запитки Ip шных камер по poe af?
ID
в общем я не знаю, как это в микроте выбрать:
IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384
ID
вот мои proposal