OP
Size: a a a
2021 October 01
теперь понятно, откуда такая щедрость)
VI
We wanted to provide you more information on the Let's Encrypt certificate expiry that occurred earlier today, September 30th 2021. Impacted customers will see attempts to connect to some websites or APIs fail with errors like "connection failed" or "issued certificate has expired".
Let's Encrypt is a Certificate Authority providing TLS certificates to many websites and services running on the Internet today. As a certificate authority, Let's Encrypt provides a certificate chain that is used by web browsers and application to validate the certificates used by websites when establishing secure TLS connections. As with all certificates, these certificate chains have an expiry date. To prepare for expiry, Let's Encrypt have been dual signing their certificate chains with both the old certificate (expiring September 30th, 2021) and a new certificate. This is one way Certificate Authorities can handle certificate expiration. While this approach has ensured that many websites and applications are not affected by the Let's Encrypt certificate chain expiry, there is a known issue with OpenSSL where the dual signing of the certificate chain was not handled correctly. OpenSSL versions prior to 1.1.0 do not properly handle dual chains and consider the chain invalid if one of the certs are expired. Additional information from the OpenSSL Blog can be found here.
For customers seeing impact with an AWS service - including AWS Lambda, AWS Elastic Beanstalk, Amazon OpsWorks, Elastic Load Balancing and Elastic MapReduce (EMR)- we are working to apply the necessary fix to the affected services. We have published updated RPMs for the affected Amazon Linux distributions. Customers running AL 2012 or AL2 can refer to this Knowledge Center article for instructions on how to update from the CDN.
Let's Encrypt is a Certificate Authority providing TLS certificates to many websites and services running on the Internet today. As a certificate authority, Let's Encrypt provides a certificate chain that is used by web browsers and application to validate the certificates used by websites when establishing secure TLS connections. As with all certificates, these certificate chains have an expiry date. To prepare for expiry, Let's Encrypt have been dual signing their certificate chains with both the old certificate (expiring September 30th, 2021) and a new certificate. This is one way Certificate Authorities can handle certificate expiration. While this approach has ensured that many websites and applications are not affected by the Let's Encrypt certificate chain expiry, there is a known issue with OpenSSL where the dual signing of the certificate chain was not handled correctly. OpenSSL versions prior to 1.1.0 do not properly handle dual chains and consider the chain invalid if one of the certs are expired. Additional information from the OpenSSL Blog can be found here.
For customers seeing impact with an AWS service - including AWS Lambda, AWS Elastic Beanstalk, Amazon OpsWorks, Elastic Load Balancing and Elastic MapReduce (EMR)- we are working to apply the necessary fix to the affected services. We have published updated RPMs for the affected Amazon Linux distributions. Customers running AL 2012 or AL2 can refer to this Knowledge Center article for instructions on how to update from the CDN.
VI
амазон тоже сам попал ) и у DO с managed базами проблемы
AO
не так давно на HN была статья с заголовком We deserve better than Confluence and Notion, https://blog.luap.info/we-deserve-better-than-confluence-and-notion.html мб это как-то связано, там в конце была реклама https://dokkument.com/
могло команду Notion что-то напугать в той статье из-за чего они вдруг решили пропустить такой баг? не знаю)
могло команду Notion что-то напугать в той статье из-за чего они вдруг решили пропустить такой баг? не знаю)
MS
MS
что с такими мудаками делать?
MS
MS
надобавляли хер знает куда
S
В спам
OP
IV
Как вам новинка от AWS анонсированная вчера - Cloud Control API?
СА
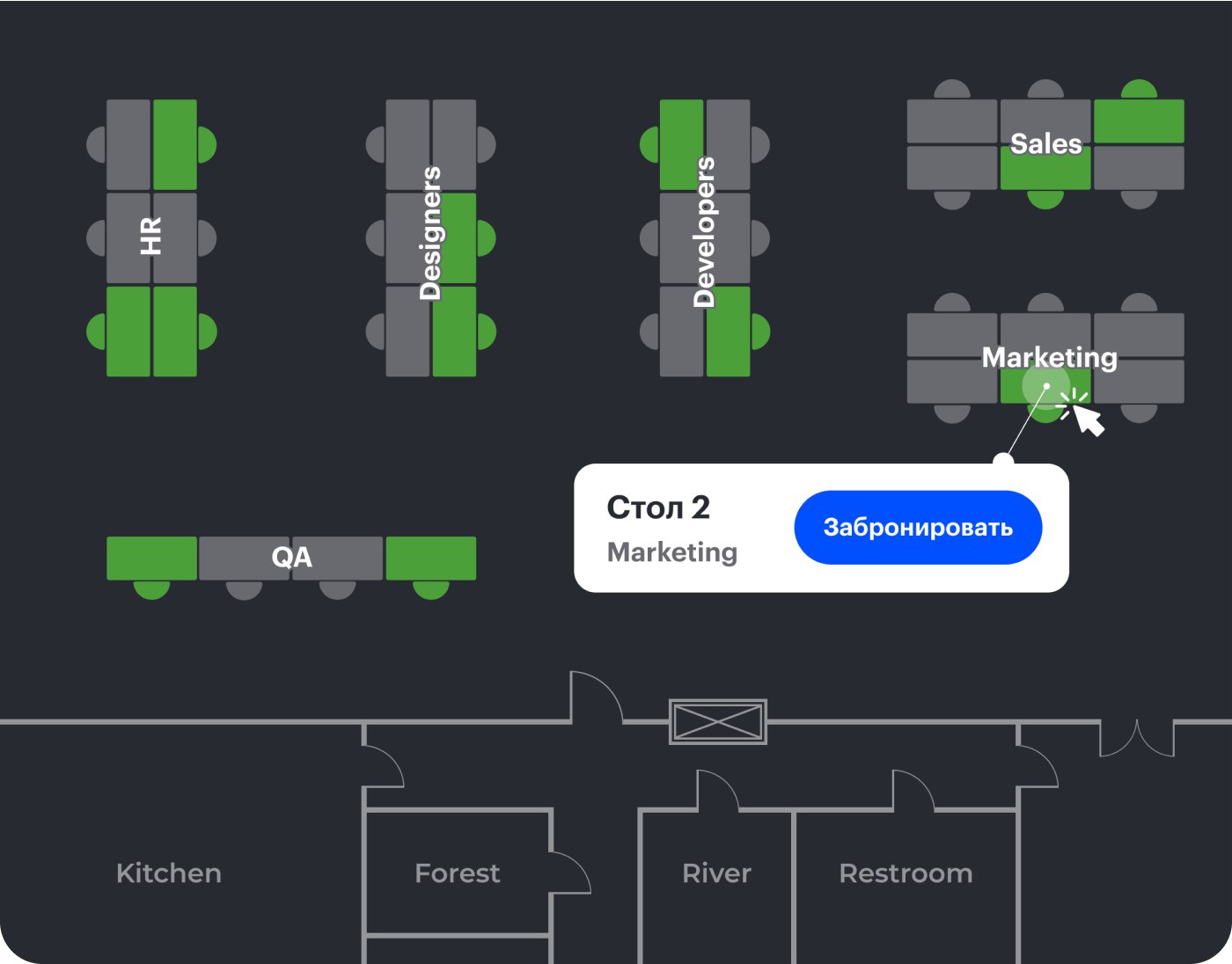
Чат, мы переехали в новый офис, который в два с лишним раза больше прежнего, и у меня проблема. Раньше у нас было 6 переговорок, и я их руками добавлял в Other calendars и мог быстро покликать и посмотреть, какая сейчас свободна. Теперь их стало 10 (или 12?), и это уже pain in the rear end. Есть какой-то лайфхак, как вывести на одном экране статус сразу очень многих ресурсов Google-календаря, или надо хакать свою собственную приблуду? За 15 минут не нагуглил ни того, ни другого(
DD
Outlook используй там удобно это.
СА
Поставить себе Outlook и подключить к Google Calendar?
O
Там же можно добавить переговорки именно как помещения, и тогда когда создаешь встречу, оно удобно подсказывает свободные. Правда это работает только в вебе
СА
Это я умею. Мне надо в целом видеть, какие переговорки когда свободны в течение дня.
СА
Без создания новых встреч.
S
DT
Эх, в яндексовом интранете это очень хорошо было сделано, минутка ностальгии 🙄
DT
Кажется, группа годная, спасибо!